Tech Insights & Updates
Stay informed with the latest IT trends, best practices, and technology insights from our experts.
Never Miss an Update
Subscribe to our newsletter and get the latest blog posts delivered straight to your inbox.
Filter by Category
More Articles
12 posts

The Cost of “Shadow IT” — and How to Stop It
Shadow IT — the use of unauthorized software and apps by employees — can expose businesses to data breaches, compliance risks, and wasted resources. This post explores how hidden technology choices create security gaps and increase costs, while outlining practical steps for identifying, managing, and preventing Shadow IT through better visibility, clear policies, and proactive IT support.

The True Cost of IT Downtime
Beyond obvious lost sales, downtime racks up massive costs from lost productivity (as all employees are idle), damage to your company's reputation, and declining employee morale. The post provides a simple formula to help businesses calculate their actual downtime cost (Lost Productivity + Lost Revenue) and contrasts the expensive, reactive "break-fix" model with the long-term, cost-saving benefits of proactive IT monitoring.
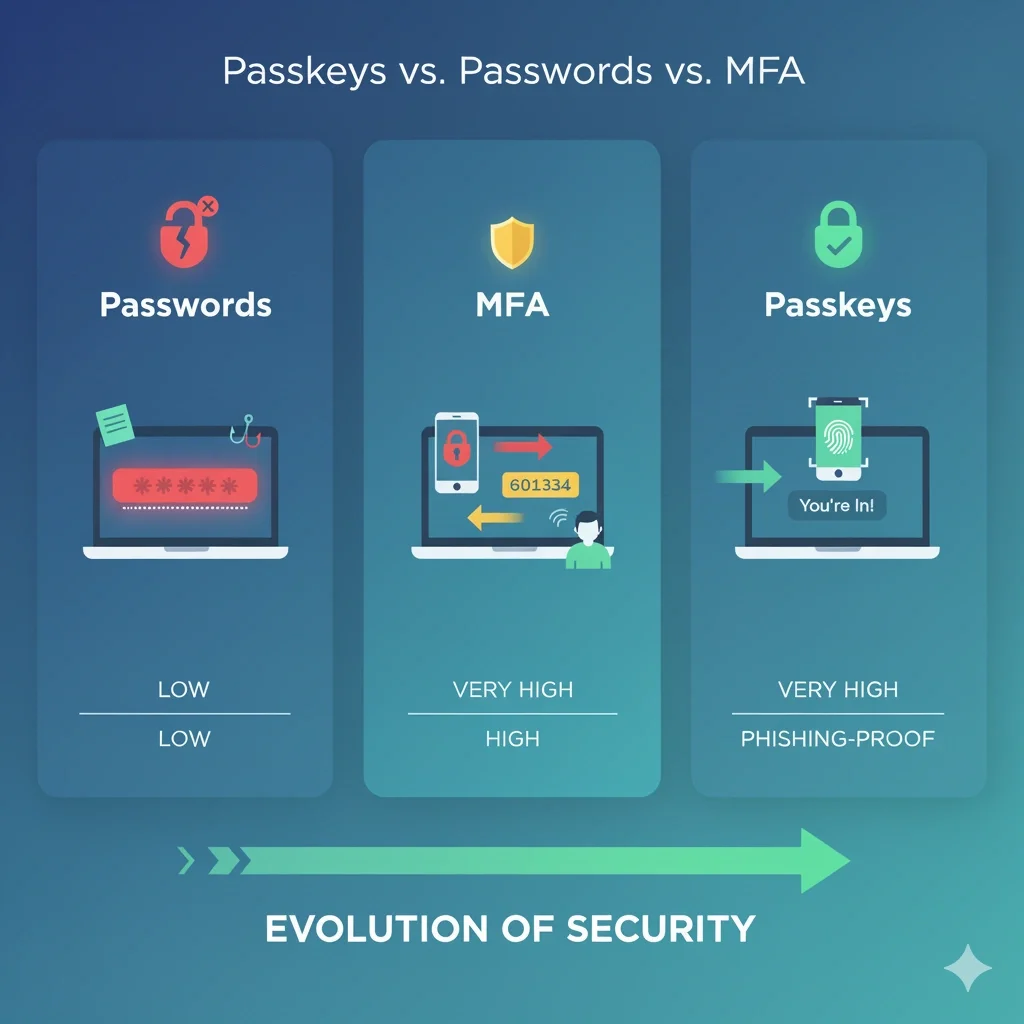
Passkeys vs. Passwords vs. MFA: What’s the Difference?
This post clarifies the key differences between passwords, Multi-Factor Authentication (MFA), and passkeys. It explains that traditional passwords ("something you know") are a weak, single layer of security. MFA improves this by adding a second, often clunky, step like a phone code ("something you have"). The post then introduces passkeys as a modern replacement for passwords, explaining how they combine two factors—"something you have" (your device) and "something you are/know" (your fingerprint, face, or PIN)—into one seamless action. The central takeaway is that passkeys are both more convenient for users and significantly more secure, as they are inherently resistant to phishing.
The Difference Between IT Support and True IT Partnership
Many businesses settle for reactive IT support — fixing problems after they happen. A true IT partnership goes further, focusing on strategy, security, and long-term growth. Learn how partnering with a Managed Service Provider like Riverside Technologies helps align technology with business goals, prevents downtime, and builds a foundation for lasting success.

Is Your Car a BYOD Risk? How Vehicles Can Become an Attack Vector
Researchers demonstrated a proof-of-concept chain in which an attack beginning near a parked car reached corporate servers by using the employee's phone as a bridge. Learn why this matters and what to do to reduce risk.

Is Your Software Vendor Putting You at Risk? The Latest Oracle Zero-Day Attack Shows Why
A recent Oracle zero-day exploit highlights the risks businesses face when relying on third-party software vendors. Many SMBs depend on tools like HR, finance, and CRM systems without realizing that vendor vulnerabilities can expose their data. This post explains how to protect your business through vendor vetting, timely patching, and ongoing monitoring of integrations.

Payroll & HR Systems Are Now an Attack Focus — Are You Vulnerable?
Payroll and HR systems have become prime targets for cybercriminals seeking financial gain and sensitive employee data. A recent “payroll pirate” campaign revealed how attackers redirect legitimate paychecks and exploit weak access controls. This post explains why even small businesses are at risk and offers five actionable steps — including access control, network segmentation, and regular audit logs — to strengthen security and protect employee data.

Why the Surge in AI-Driven Cyberattacks Means Your Business Needs to Reassess Security
Artificial intelligence is changing cybersecurity—both for defenders and attackers. Recently, cyber criminals have begun using AI tools to automate phishing, create convincing fake emails, and identify system weaknesses faster than ever. This shift means that small and mid-sized businesses are becoming easier targets, as AI makes attacks more scalable and harder to detect. The post explains how AI-powered threats differ from traditional ones and provides five key steps businesses can take right now to protect themselves, including staff training, multi-layered security, and proactive monitoring.

Empowering Business with AI: Security, Compliance & Microsoft Copilot
Artificial Intelligence (AI) is no longer a futuristic concept—it's a transformative force reshaping how businesses operate, innovate, and compete. From automating routine tasks to enhancing decision-making, AI offers immense potential. However, with this power comes responsibility, especially in maintaining cybersecurity and regulatory compliance. Strategic Applications of AI in Business AI ...

The Top 5 Signs Your Business Has Outgrown Its Current IT Setup
The Top 5 Signs Your Business Has Outgrown Its Current IT Setup Author: Lewis Hancock | Date: October 13, 2025 Technology should empower your business — not hold it back. But as your company grows, so do your IT demands. What once worked perfectly when you had five employees might ...

SonicWall Cloud Backup Breach: What It Means for Your Business
A recent breach in SonicWall's cloud backup service exposed configuration data for all users. Learn what happened, what it means for you, and how to protect your business.
